“He should rightly divide and must understand the definitions and distinct differences of cybersecurity, cybercrime, cyberdefense, cyberwarfare and information security.” BGen Nicolas Ojeda ‘77 Signal Corps (Ret), the former co-chair of NCIAC.
Published in the Cavalier Magazine, Oct-Dec2024 Issue (pages 45-47)
By J. Irving
Now, I can fully retire and let this article be my last hurrah, as a cybersecurity professional.
I was unlucky. Someone else got hired for the position of Deputy Director General (DDG) for Cyber and Emerging Threats (DCET) at NICA that the President created on January 2024 by virtue of EO#54.
On creating a critical impact, I am worried in what I heard in the grapevine. The one taking over is a noob. Someone pointed out that he is coming from an ISP business, legislative sector and PAF service. Another critic said, he is just a wide reader, YouTuber and a theologist, without any hands-on practice or certifications to show. There are other things said that are unprintable. Now, our country would let him defend our cyberspace from state sponsored hackers, who are highly skilled individuals, no longer against a hooded kid in a basement.
I already congratulated the new DDG and sent this notion, offering suggestions that I think could be undertaken in his capacity as DCET. He thanked me. I offered him my help. I told him that I am glad though that he was the one selected, being young and energetic. As a fellow Peemayer, I hope that he may heed my unsolicited advice extended with the best of intentions.
To put things in the proper perspective, I do not begrudge his appointment. For me, he can rise as a leader with renowned experts in the industry, around him, as consultants (one of them is Angel Redoble, the former CISO of PLDT, as he proudly announced his new position in LinkIn). The new DCET is a very charismatic speaker in interviews and cybersecurity fora. He has his own support system – the PICSPro. As a former congressman, he may have the ears of government functionaries. Thus, he will be able to deliver and make things happen for us. I wish him luck and hoping he will consider these suggestions and eventually emerge as the messiah that we have all been waiting.
My mistah, Police General Gil Pacia ‘80, who used to be the IT whiz of NICA and who applied also for the job, had dreamt of setting up his forensics, ethical hacking, VAPT, SOC, CERT and cyber threat intel assets. I said no, “Kailangan lang natin LAWAY” (pardon the word). I told him this opportunity is too good to pass up, I can be his assistant. PARA SA BAYAN!
I had thought of volunteering for the job because there is a shortage of cybersecurity professionals and wanted to offer a best option. I felt my time is running out. I am getting older and there will be no more next time. I believe I still have many things to share, in solving cybersecurity problems that the national government has overlooked and neglected.
General Pacia and I possess already the necessary security clearances. We were both experienced heads of IT units, as well as intel-eligible, trained investigators and most importantly, belong to the SIGNAL CORPS, where cyber combatants emanate.
You may wonder, what motivates me to shun retirement? Well, cybercrime is everywhere and growing. Such as the recent global outage that paralyzed hospitals and airlines, or government sites being defaced. Even the website of CBCP was vandalized. Walang patawad. Even the Honda service center workstations, where I had my CR-V checked, went down. Lahat na lang!
Perhaps, you can relate better with this example. You, or someone you know, had their Facebook account hacked. The scammers then ask money, using a variety of pretext, from friends of victims via GCash transfers. Like Fr. Gerard Deveza, a gifted healer and the founder of a school for indigents, who lost almost a million of cash donations. I reported the incident to CICC, but nothing came out of it. We all are hapless and helpless; we are on our own. The best thing we can do is to warn the public that our FB accounts were hacked, with a comforting discovery who our true friends really are, when they sent money to the scammers, thinking it was us, without asking any questions. For the hackers, it’s business as usual, trolling for the next victim, parang wala lang! There is no stopping them, much less hunting them down.
I read the National Cyber Security Plan (NCSP) 2023-28 over and over – looking for answers. In my opinion, the NCSP lacks coordinating instructions, something similar to military OPLANs; and sadly, things still exist just on paper. The NCSP was crafted and enacted into law before the creation of DCET. As such, there is no mention of DCETin NCSP 2023-28, a key player, much more a focal point.
Therefore, let us start. For the designated DCET, I suggest these coordinating instructions:
1. First and foremost, invoke EO#189 of 2015 and EO#95 of 2019, that mandated the creation of the National Cybersecurity Inter-Agency Committee (NCIAC). It is composed of the Executive Secretary as chair with DICT and NSC as co-chairs, with committee members from DOE, DOF, DFA, DILG (to include PNP), DOJ (to include NBI), DND (to include AFP/PA/PN/PAF), DOTr (to include CAAP & PCG), PCOO (as spokesperson), NTC, NPC, ATC, CICC (as Secretariat) and BSP (not Boy Scout). I recall BGen Nicolas D. Ojeda ’77, Signal Corps (Ret) of the defunct ICT Office who once presided over meetings during pre-DICT days. In one meeting, the NBI reported that the hackers responsible for the COMELEC breach were already under their custody, before the news broke out. This is the kind of NCIAC that must be revived, a clear-cut instance of management by objective (MBO), and not about procedures and strategies, as enunciated in the NCSP. (As a footnote, Senator Imee Marcos has seen the importance of NCIAC and she is proposing in her Senate Bill number 1365 dated 5 October 2022, an act institutionalizing NCIAC by renaming it to National Cybersecurity Council)
2. The task of co-chairman held by National Security Council (NSC) can be delegated to the DCET, co-chairing with DICT (the USec for Cybersecurity). With this arrangement, the DCET can now preside and orchestrate its work at NCIAC, just like General Ojeda.
3. DCET can evolve the fight from exclusively cyber to a hybrid form, incorporating effective kinetic solutions. The government must do something dramatic, like what the Israelis did to Hamas, with a stark reminder that they can track the Hamas hackers and can pinpoint their exact whereabouts, thereby instilling fear. It does not mean bombing the hackers’ lairs, but to apprehend those who have committed cybercrimes, charge them in court and hopefully secure convictions. If cybercriminals are based abroad, then work with international law enforcement arms.
4. At NICA, as its primary task, DCET must build up the National Cybersecurity Threat and Database which highlight types of threats, vulnerabilities and mitigation strategies, to include dossiers of hackers and scammers with their identified IP addresses, and to include, counterintelligence. Conduct workshops as well, focusing on the Order-of-Battle (OB) to identify and then neutralize the notorious groups, such as: Anonymous, Pinoy Vendetta, Medusa, Dark Pink, Pinoy LulzSec, DeathNote, to name a few. Then, consider intel-sharing with local and international agencies, as DCET needs the help of everyone, utilizing Human Intelligence (Humint) network in completing the cycle of intelligence: planning and direction, collection, processing and exploitation, analysis and production, and dissemination and integration…
5. DCET must place under his guidance all military cybersecurity assets, to avoid duplication and competition among them, as pointed out by General Pacia that these units will all acquire his wish-list; better, divide the list and let each one specialize. DCET must manage, improve teamwork and follow-up deadlines:
a) The Office for Cyber and Information Systems Management (OCISM) at DND. The Department has virtual machines for sandboxing of ransomware (the number one and most feared cyber-attack) and other malware. The office possesses the names of members and points-of-contact of Experts Working Group (EWG) for Cybersecurity of the ADMM+, composed of ASEAN countries plus Australia, China, India, Japan, New Zealand, Republic of Korea, Russia and the United States. They exchange Subject Matter Experts (SMEs) among them. The office is also working for the creation of the Department for Cyber Warfare in PMA, where future military leaders should be taught with the Tallinn Manual, about the rules of engagement in cyberspace, jus ad bellum.
b) AFP-Cyber Group. This will be the future Cyber Command that is envisioned in the NCSP. The unit can best be described as bug and threat hunters. Likewise, it can be a proponent for the creation of Philippine Cyber (PC), a new branch-of-service, in the same level as PA, PN and PAF – for joint and combined operations.
c) Army Cyber Battalion, Army Signal Regiment (ASR), PA. DCET must understand the definitions and distinct differences of cybersecurity, cybercrime and cyber defense. As a cyber defense unit, the Army should be deep in the Dark Web for cyber espionage, terrorism (recruitment of radicals) and hacktivism. The unit essentially is the guardian of the Army Comm Systems. One Army – One Network.
d) Naval Information & Communications Technology Center (NICTC), PN. It already has cyber range and trained CERT. Its personnel secure the National Coast Watch Center, while the Center monitors the WPS.
e) 950th Cyberspace & Electronic Warfare Wing (P), PAF. DCET must support its regularization from a provisional status. The unit primarily protects from cyber-attacks our Air Control Systems and Air Defense Systems that monitors and counters unidentified aircraft entering our jurisdiction; control of inbound and outbound commercial planes is the concern of CAAP (as office of DOTr, a representative may also sit at NCIAC). In January 2021, PLDT-Smart President Manny Pangilinan funded the groundbreaking for the building that will house the Cybersecurity Center for Excellence. The Center will develop standard and best practices in cybersecurity, with the goal of partnership between private and government officials in having basic literacy, fluency and eventually, mastery in cybersecurity.
6. DCET must encourage the above-mentioned cyber units of the different branches-of-service to recruit IT professors and CISO from private corporations to join their respective Ready Reserve Forces. In the Army, we have COL ROLAND J. ONG, MNSA PA (RES), the Head of Cybersecurity Architecture, Asperiq based in Switzerland; and LTC JANNETTE C. ARCEO, MNSA PA (RES), a female battalion commander in a Ready Reserve and a lecturer in cybersecurity, hailed as ASEAN Top Women In Security. Make use and take care of them. In recruiting professors from schools and universities, DCET can gain access to their talented and gifted students – offering them opportunities to serve our country.

7. DCET must take control of National Cybersecurity Coordination Center (NCCC), composed of officials from member agencies of NCIAC. The NCCC does not need to be housed in NICA, as everything can be done virtually, online. Find a way to receive incoming reports from informers and whistleblowers by phone or email. A combat scoreboard can be published in the web (answering the five W’s and one H) with corresponding statistics of success, or failure … in order that the public may be updated, and their confidence level be uplifted regarding our improving cybersecurity situations; likewise, the news on police works will deter would-be black hat hackers to commit cybercrimes.
8. DCET must volunteer to become an ex-officio member of the Cybersecurity Committee of the Armed Forces of the Philippines Multi-Sectoral Governance Council (AFP MSGC), to keep the committee informed as well as to garner their support.
9. DCET must establish a close working relationship with Facebook and other social media platforms where scammers thrive. Facebook must find ways to block fake news that have proliferated in the platforms. Canada, for instance, has found ways to eliminate certain links in Facebook. Moreover, as mid-term elections is upon us and the Presidential election in USA, Facebook must be vigilant for cloned accounts misused as trolls (sock puppets). There should be a way for complainants to remove fake accounts.
10. DCET should make permanent contact with the Cybersecurity Tech Accord, composed of global technology vendors, to alert us and be able to immediately patch glitches, similar to the CrowdStrike mishap.
11. DCET must buck up RootCon, the premier hacking conference in the Philippines. This will be the prime source for professionals with the best skills. I suggest DCET should attend the DefCon in Las Vegas to observe how G-men there take advantage of such events and understand that everything is hackable!

12. For legal matters, establish rapport and foster cooperation with the DOJ, through the Office of Cybercrimes and the National Bureau of Investigation – Cybercrime Division, to run after cybercriminals. The NBI-CCD operatives are armed with warrants to search, seize, and examine computer data. These are the actions they made to run after the POGO operators.
13. The Philippine National Police Anti-Cybercrime Group, PNP-ACG. This group process direct complaints in their regional offices or through official channels. The public, specially Cybercrime victims, must know this.
14. Should the DCET require assistance from Telcos regarding smishing, vishing and other phishing tricks in cellphones, there are Peemayers at Globe, PLDT-Smart, Dito and PT&T – as I have given their names to him. All are willing to help him!
15. Lastly, always Be prepared to conduct Special Operations.
In summary, my comprehensive advice covered the five pillars of cybersecurity: Legal, Technical, Organizational, Capacity Development and Cooperation. In the recent Global Cybersecurity Index (GCI 2024 5th Edition), which measured our commitment to cybersecurity, the Philippines is ranked 53rd out of 194 countries.
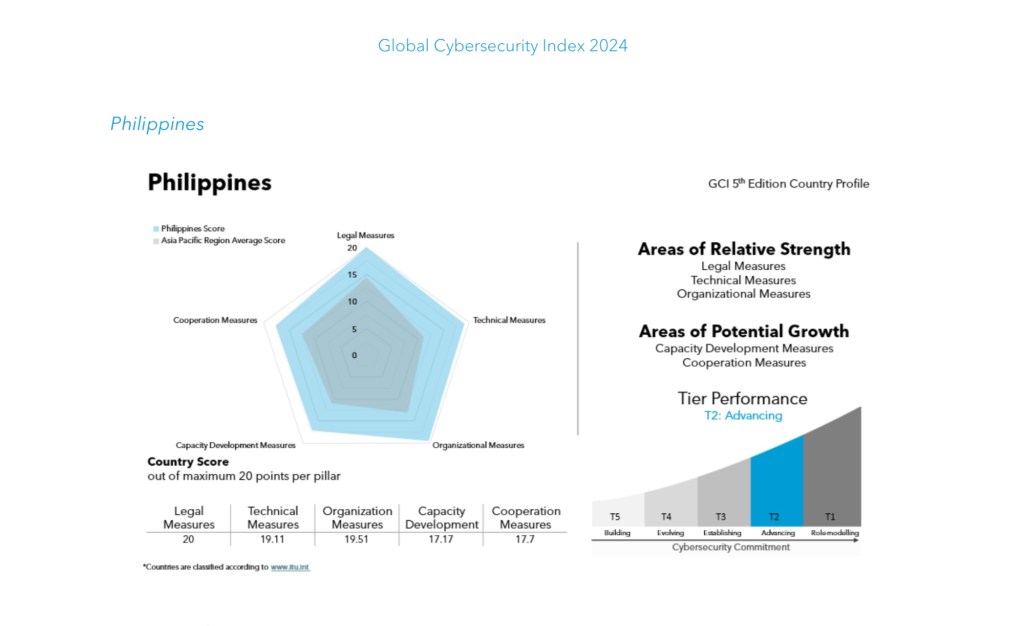
With the success of DCET, our GCI rating will improve, to assure Filipino citizens their safety and protection in cyberspace is guaranteed, in line with the vision of PBBM and DICT to realize a One Digitized Government, One Nation.
Let us give our full support to the appointed DCET and feed him with A1 information because his success is our success …
An arrest a day, keeps hackers away!